Ever clicked on a website and noticed that little padlock icon next to the URL? That small symbol represents a massive, intricate process working tirelessly behind the scenes to protect your data. It’s the visual cue for Transport Layer Security, or TLS. For a modern web developer, understanding this technology is no longer a “nice-to-have”—it’s a core competency. If you’re ready to finally learn about TLS encryption and demystify what happens when a browser and server connect securely, you’re in the right place.
This guide will break down everything you need to know. We’ll explore what TLS is, how it evolved from SSL, walk through the crucial TLS handshake step-by-step, and discuss how you can implement it effectively. Let’s secure your knowledge.
What Is TLS Encryption, Really?
At its heart, Transport Layer Security (TLS) is a cryptographic protocol designed to provide secure communication over a computer network. Think of it as a secure, armored tunnel for information traveling between a user’s web browser (the client) and the website’s server.
When data is sent over the internet without TLS, it travels as plaintext. This means anyone snooping on the network—like a hacker on a public Wi-Fi network—could easily read, steal, or even modify the information. TLS prevents this by ensuring three key things:
- Encryption: It scrambles the data so that only the client and server can understand it. Even if intercepted, the information is just gibberish to an attacker.
- Authentication: It verifies that you are connected to the correct server and not an imposter. The padlock icon is your assurance that the website is who it claims to be.
- Integrity: It ensures that the data has not been tampered with or altered during transit. It uses message authentication codes (MACs) to check for any modifications.
Without TLS, sensitive information like passwords, credit card numbers, and personal messages would be dangerously exposed. That’s why modern web development mandates the use of HTTPS (Hypertext Transfer Protocol Secure), which is essentially the standard HTTP protocol layered on top of TLS.
SSL vs. TLS: Clearing Up the Common Confusion
You’ve probably heard the term SSL (Secure Sockets Layer) used interchangeably with TLS. While they serve the same purpose, they aren’t the same thing.
SSL was the original encryption protocol developed by Netscape in the mid-90s. However, significant security vulnerabilities were discovered in its various versions (SSL 2.0, SSL 3.0). In response, the Internet Engineering Task Force (IETF) took over and released an upgraded, more secure version called TLS 1.0 in 1999.
Think of TLS as the direct successor to SSL. All versions of SSL are now officially deprecated and considered insecure. Any modern, secure website uses TLS, even if people colloquially refer to it as “getting an SSL certificate.”
Here’s a quick breakdown of the versions:
- SSL 1.0: Never publicly released.
- SSL 2.0 & 3.0: Deprecated and insecure.
- TLS 1.0 & 1.1: Deprecated since 2021 due to known vulnerabilities.
- TLS 1.2: The current workhorse and a widely supported secure protocol.
- TLS 1.3: The latest, fastest, and most secure version, offering simplified handshakes and stronger ciphers.
As a developer, you should always configure your servers to support TLS 1.2 and preferably TLS 1.3 while disabling all older SSL and TLS versions. [external link: Mozilla’s guide to server-side TLS configurations].
How TLS Works: The Handshake Explained Step-by-Step
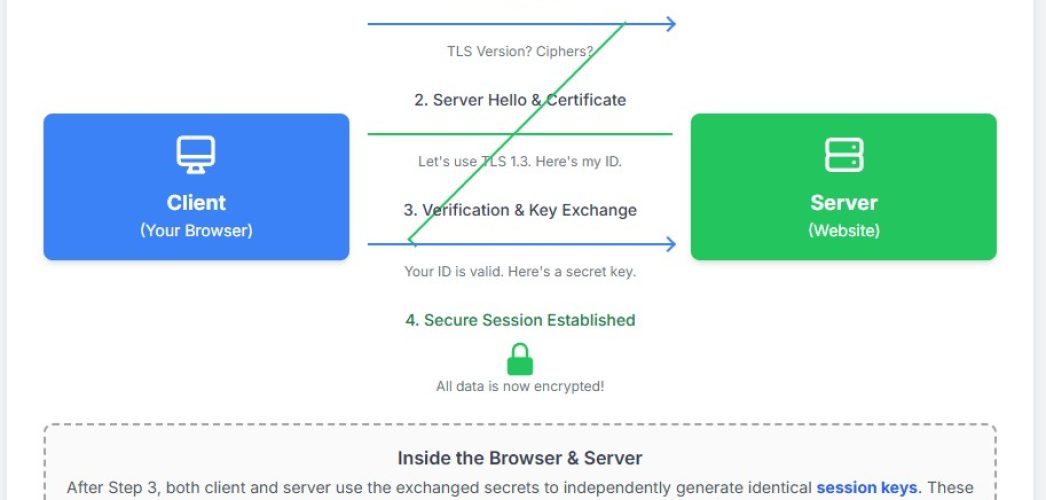
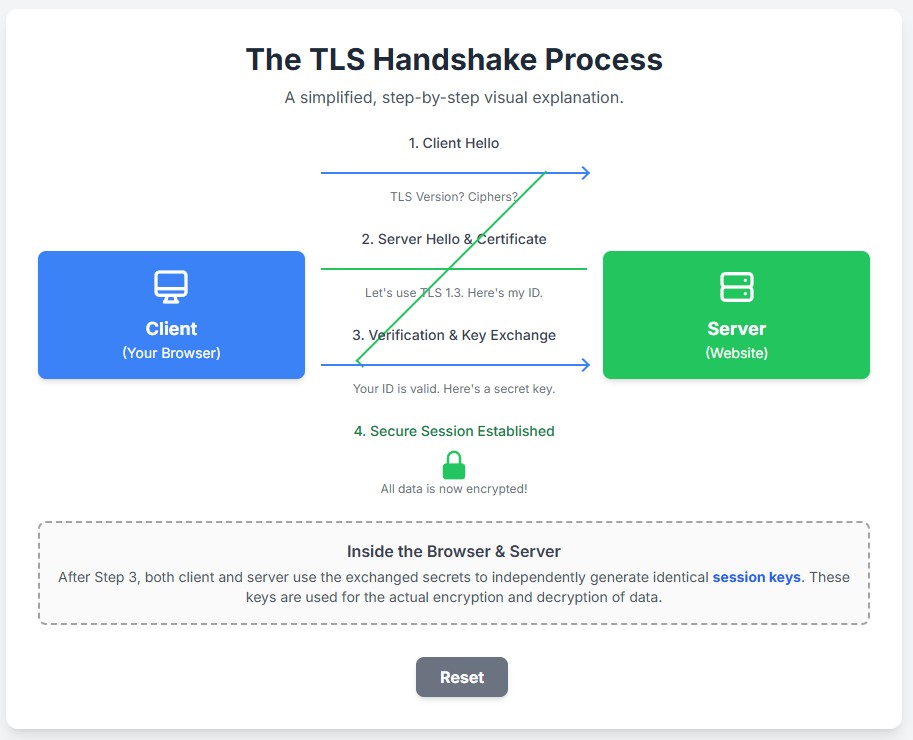
The magic of establishing a secure connection happens during a process called the TLS handshake. It’s a series of back-and-forth messages between the client and the server to negotiate the terms of their secure session before any actual application data is exchanged.
Imagine you want to send a secret package. The handshake is like you and the recipient first agreeing on a special lock, exchanging keys, and verifying each other’s identities before you actually send the package.
Here’s a simplified breakdown of the process for TLS 1.2:
Step 1: The ‘Client Hello’
The conversation starts with your browser (the client) sending a “Hello” message to the server. This message isn’t just a friendly greeting; it contains crucial information:
- The TLS versions the client can support (e.g., 1.2, 1.3).
- A list of cipher suites it can use. A cipher suite is a set of algorithms that defines how encryption, authentication, and integrity checks will be performed.
- A random string of bytes called the “client random.”
Step 2: The ‘Server Hello’ and Certificate
The server receives the client’s message and responds with its own “Hello.” In this response, it:
- Confirms which TLS version it has chosen from the client’s list.
- Selects one cipher suite from the client’s list that it also supports.
- Provides its own “server random” string of bytes.
- Sends its TLS certificate (often called an SSL certificate). This certificate contains the server’s public key and has been digitally signed by a trusted Certificate Authority (CA), which vouches for the server’s identity.
Step 3: Authentication and Key Exchange
This is where the client verifies the server’s identity and the secure key is created.
- Certificate Verification: The client’s browser checks the server’s certificate. It confirms that the certificate is valid, hasn’t expired, and was issued by a CA the browser trusts. This proves the website is legitimate. [internal link: What is a Certificate Authority?]
- Key Exchange: The client generates another random string of bytes, called a “premaster secret.” It encrypts this premaster secret using the server’s public key (which it got from the certificate). Because it’s encrypted with the public key, only the server, with its corresponding private key, can decrypt it.
- Session Keys Created: Both the client and the server now have the same three pieces of information: the client random, the server random, and the premaster secret. They independently use these to calculate the same set of unique session keys. These keys will be used to encrypt and decrypt all the data for the rest of the session.
Step 4: Secure Communication Begins
To finalize the handshake, both client and server send a “Finished” message, which is encrypted with the newly created session key. This confirms that the handshake was successful and that everything from this point forward will be symmetrically encrypted.
The armored tunnel is now open! Your browser can now send its HTTP request (e.g., to load a webpage), and the server can send its response, with all data fully protected.
Why TLS 1.3 is a Game Changer
While TLS 1.2 is secure, TLS 1.3 made significant improvements. Its main advantage is speed. The TLS 1.3 handshake is much faster, requiring only one round-trip instead of two. This reduces latency and makes websites load quicker, which is crucial for user experience and SEO.
It also enhances security by removing obsolete and weak cryptographic algorithms, making it much harder to misconfigure and leave vulnerabilities open. If your infrastructure supports it, prioritizing TLS 1.3 is a major win.
How Infineural Technologies Simplifies Secure Development
As you can see, properly configuring TLS, managing certificates, and keeping up with the latest security standards can be complex and time-consuming. A single mistake in choosing a cipher suite or letting a certificate expire can bring your application down or expose your users to risk.
This is where the right tools and infrastructure make all the difference. At Infineural Technologies, we believe developers should be free to innovate and build amazing features, not get bogged down in security configuration.
Our managed cloud platform is engineered for security from the ground up. We handle the heavy lifting for you:
- Automated TLS Configuration: We automatically enforce the latest secure TLS protocols (including TLS 1.3) and ciphers, so you don’t have to.
- Effortless Certificate Management: Our platform includes free, auto-renewing TLS certificates for all your applications. Say goodbye to manual renewals and expiration warnings.
- Optimized Performance: By leveraging features like the faster TLS 1.3 handshake, our infrastructure ensures your applications are not only secure but also lightning-fast.
By building on Infineural Technologies, you can be confident that your application’s data transfer is protected by industry-leading security practices, allowing you to focus on what you do best: coding.
Take Control of Your Web Security
Understanding how TLS works is a fundamental skill for any developer building for the modern web. It’s the protocol that underpins trust and privacy across the entire internet. By grasping the concepts of the handshake, the role of certificates, and the evolution from SSL, you are better equipped to build robust, secure, and trustworthy applications.
Ready to stop worrying about TLS configurations and focus on building your next big thing?
Contact Infineural Technologies today for a free consultation. Let’s build a more secure web, together.